
Trellix Network Security
Detect, block and respond to advanced, targeted, and other evasive attacks.
Effective protection against cyberbreaches for midsize to large organizations
Trellix Network Security is an effective cyberthreat protection solution that helps your organization minimize the risk of costly breaches by accurately detecting and immediately stopping advanced, targeted, and other evasive attacks hiding in internet traffic. It facilitates efficient resolution of detected security incidents in minutes with concrete evidence, actionable intelligence, and response workflow integration.
With Network Security, your organization is effectively protected against today’s threats, whether they:
- Exploit Microsoft Windows, Apple OS X operating systems, or application vulnerabilities
- Are directed at the headquarters or branch offices
- Are hidden in a large volume of inbound internet traffic that must be inspected in real time
At the core of Network Security are the Trellix Multi-Vector Virtual Execution (MVX) and dynamic machine learning and artificial intelligence (AI) technologies.
MVX is a signature-less, dynamic analysis engine that inspects suspicious network traffic to identify attacks that evade traditional signature- and policy-based defenses. Multiple machine learning, AI, and correlation engines represent a collection of contextual dynamic rules engines that detect and block malicious activity in real time and retroactively, based on the latest machine, attacker, and victim intelligence. Network Security also includes intrusion prevention system (IPS) technology to detect common attacks using conventional signature matching.
Trellix Network Security is available in a variety of form factors and deployments and performance options. It’s typically placed in the path of internet traffic behind traditional network security appliances such as next-generation firewalls, IPS, and secure web gateways (SWGs) to detect both known and unknown attacks with high accuracy and few false positives, while facilitating an efficient response for each alert.
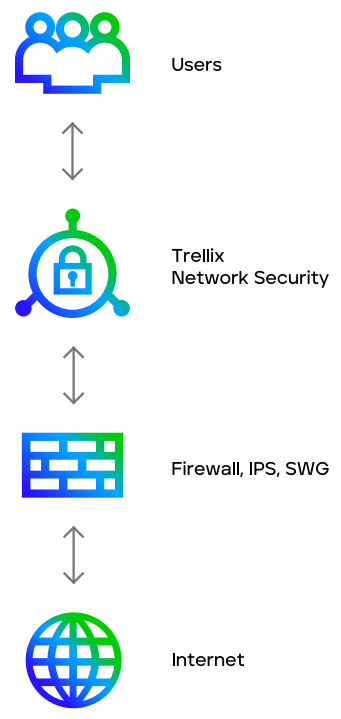
Typical configuration of Network Security solutions
Physical Appliances
Virtual Appliances
Virtual Execution Smart Grid

Benefits
- Leave No Attack Unseen with Network Detection and Response (NDR)
Gain unparalleled visibility and apply state-of-the-art, signatureless detection and protection against the most advanced and evasive threats, including zero-day attacks. - Respond to Alerts That Matter
Improve analyst efficiency with high-fidelity alerts that trigger when it matters most, saving time and resources and reducing alert volume and fatigue. - Automate and Simplify Security Workflows
Generate concrete real-time evidence and Layer 7 metadata to provide further security context to pivot to investigation and alert validation, endpoint containment, and incident response.
Features
Identify Attacks that Evade Traditional Defenses
Detect multi-flow, multi-stage, zero-day, polymorphic, ransomware and other advanced attacks with signature-less threat detection.
Leverage ML/AI and Correlation Engines for Retroactive Detection
Detect known and unknown threats in real time while also enabling back-in-time detection of threats.
Detect Suspicious Lateral Movements
Track and block lateral threats propagating within your enterprise network to reduce post-breach dwell time.
Categorize Non-Critical Riskware
Separate critical and non-critical malware (such as adware and spyware) to prioritize alert response.
Block Attacks Inline in Real Time
Immediately stop attacks to improve efficiency and minimize the impact of security incidents.
Map Detected Threats to MITRE ATT&CK Framework
Map detected threats to the MITRE ATT&CK framework for contextual evidence and future containment and remediation.
Cover Expanding Attack Surfaces
Protect your diverse network environment with support for the most common operating systems and over 160 file types.
Protect Your Network Anywhere
Choose from an extensive set of deployment scenarios, including in-line and out of band, on-premises, hybrid, public and private cloud, and virtual offerings.
Get to know the Trellix Ecosystem
The Trellix Platform learns and adapts for living protection while delivering native and open connections and providing expert and embedded support for your team.















