
Defend all your mobile devices
Protect your employees and their mobile devices with Trellix Mobile Security. This solution detects threats and vulnerabilities on Apple iOS or Google Android devices, the networks they’re connected to, and the applications that users have downloaded. On-device detection capabilities provide protection whether the device is online or not.
Mobile Security uses machine learning capabilities fed by billions of data points from millions of devices to identify current or imminent threats and attacks, including ones that have never been seen before.
Key benefits
- Optimal mobile security provides on-device, real-time protection that detects mobile threats and protects against zero-day attacks
- Protection that highlights privacy risks in applications to protect users and ensure they are aware of the dangers associated with any given application
- Enterprise-grade actionable mobile threat intelligence to help you better understand and quickly respond to mobile threats
- Compliance controls for mobile devices, allowing your employees to work anywhere, any time, and on any device
- Protection for users against phishing by detecting harmful links found in text messages, social media apps, and emails
- Integration with EMM solutions, but also works in BYOD scenarios with automated actions that are triggered when threats and vulnerabilities are discovered
- Incident response teams can take advantage of deep threat forensics for analysis and action to prevent a compromised device from turning into an outbreak
Mobile device threat detection and protection
Always-on Mobile Security
Unlike cloud-based mobile security solutions that rely on app sandboxing or traffic tunneling, Trellix Mobile sits directly on mobile devices to provide always-on protection no matter how a device is connected—via a corporate network, public access point, or cellular carrier, and even offline.
Advanced Threat Analysis
Machine learning algorithms analyze device behavior deviations to uncover indicators of compromise and accurately identify advanced device, application, and network-based attacks.
A Single Management Console
Extend visibility and control of mobile devices from the same console managing OS-based endpoints, servers, containers, and embedded IoT devices.
Product Tour
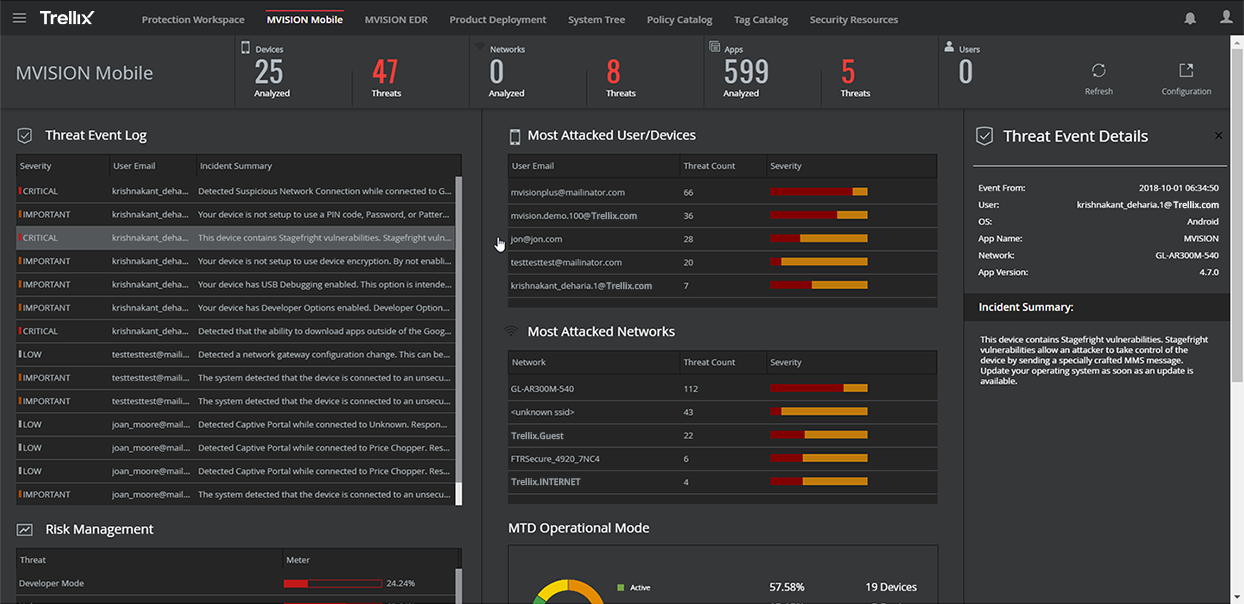
A central administration mobile security console provides security administrators overall visibility, policy management, and dashboards.
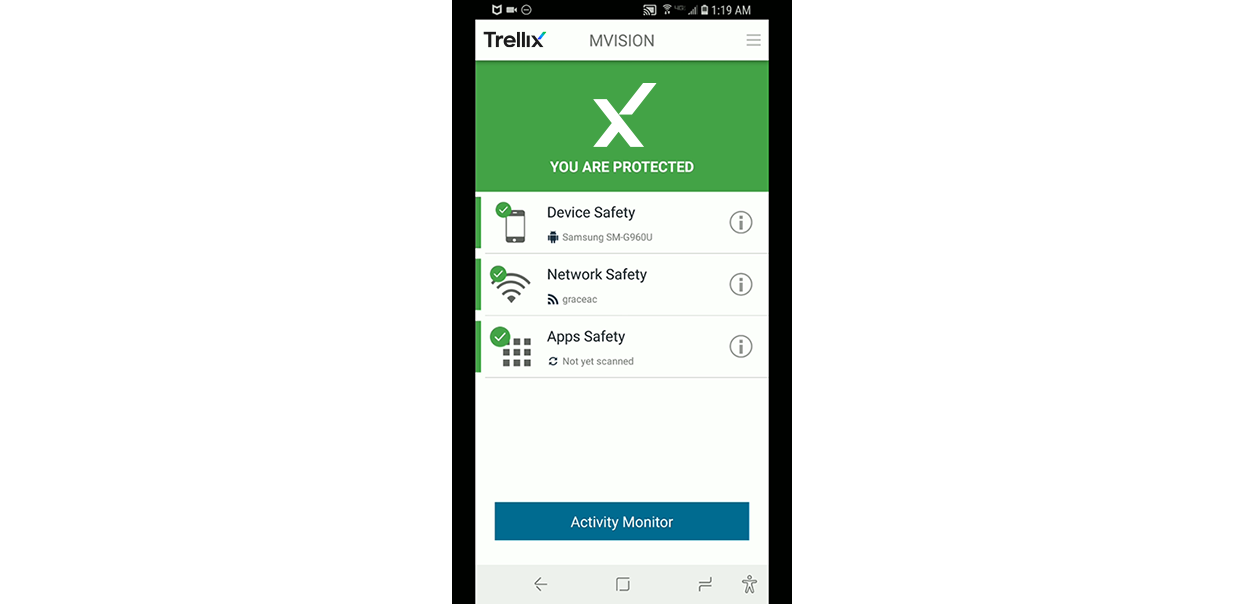
Your mobile users get a straightforward view of their security status.
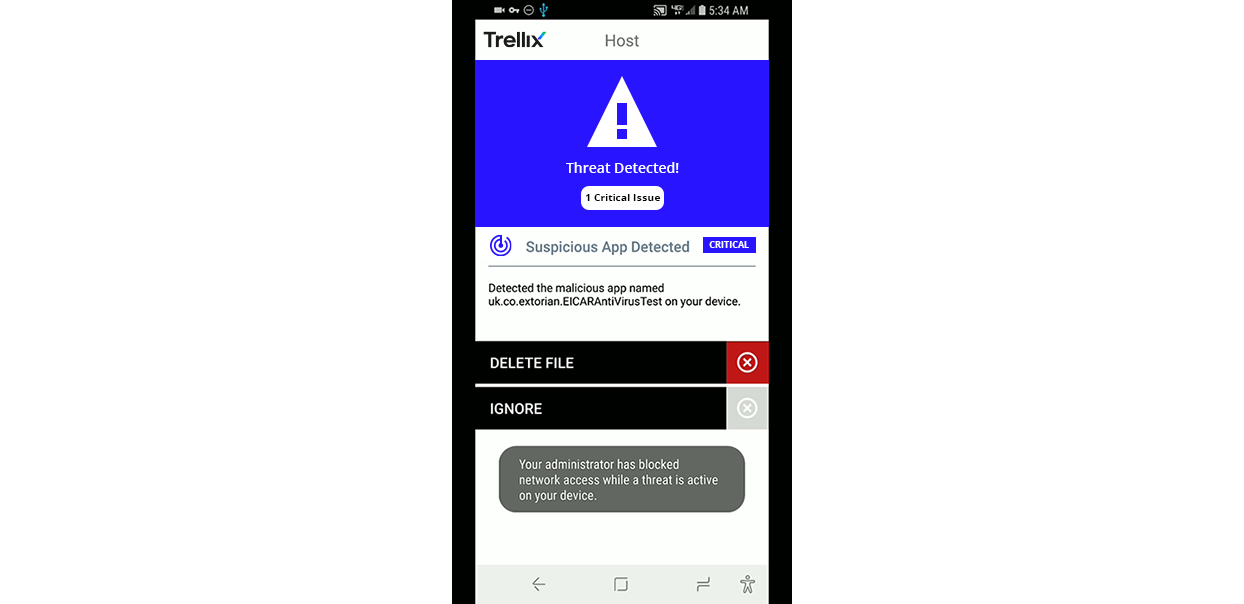
Threats are centrally logged and an immediate notification is sent to the mobile device.
Product Features
Securely Enable BYOD
Leave employees to their own devices and accommodate the human factor, without compromising the user experience or violating privacy.
On-Device Protection
Trellix Mobile secures Android and iOS devices, including iPhones and iPads.
Detailed Forensics
Incident response teams can take advantage of deep threat forensics for analysis and action to prevent a compromised device from turning into an outbreak.
Phishing Protection
Protect users against phishing by detecting harmful links found in text messages, social media apps, and emails.
Compliance Controls
Allow your employees to work anywhere, any time, on any device.
EMM Integration
For organizations with more than one enterprise mobility management (EMM) solution, Trellix Mobile integrates with your environment.
