
Trellix Data Loss Prevention
Protects sensitive information across top threat vectors.
Protect against intentional and accidental data leaks
Data loss is one of the greatest threats to organizations today. A breach can financially ruin an enterprise, not to mention the potential irreparable reputational harm. At the same time, not all information can or should be protected. That’s where Trellix Data Loss Prevention (DLP) comes in. With exceptional visibility across data types and throughout the data lifecycle, organizations can find sensitive information and intellectual property, classify only the data that requires added protection, determine policies to be applied across the environment, and detect inappropriate activity for remediation.
With Trellix DLP, out-of-the-box options for policies and reports that map to common compliance frameworks make it easy to pass the next audit or regulatory review. Open architecture makes it easy to integrate with third-party tools like SIEM and SOAR to ensure that incidents can be managed effectively from end to end. With a central, unified console, available on-premises or via SaaS, enterprises will benefit from streamlined and simplified administration for policies, event detection, reporting, and more.
Trellix DLP protects top data leak vectors and across 400+ content types
- Workstations (Laptops/ Computers)
- Network
- Web
Comply with multiple regulatory and industry standards, including
- Privacy
- Payment information
- Healthcare
- Financial reporting
DID YOU KNOW ...
Trellix Data Security statistics
400+
File formats supported by Trellix Data Loss Prevention24M+
Drives protected worldwide by Trellix Data Encryption700+
Patch protections delivered by Trellix Database SecurityWhy Trellix Data Loss Prevention?
![]()
Protect Against Insider Risk
Prevent data exfiltration. Coach end users attempting to violate policy.
![]()
Quickly Demonstrate Compliance
Out-of-the-box rules and reporting aligned with key regulatory frameworks.
![]()
Manage Information Footprint
Find, classify, and protect the data that matters to your organization.
Product Features
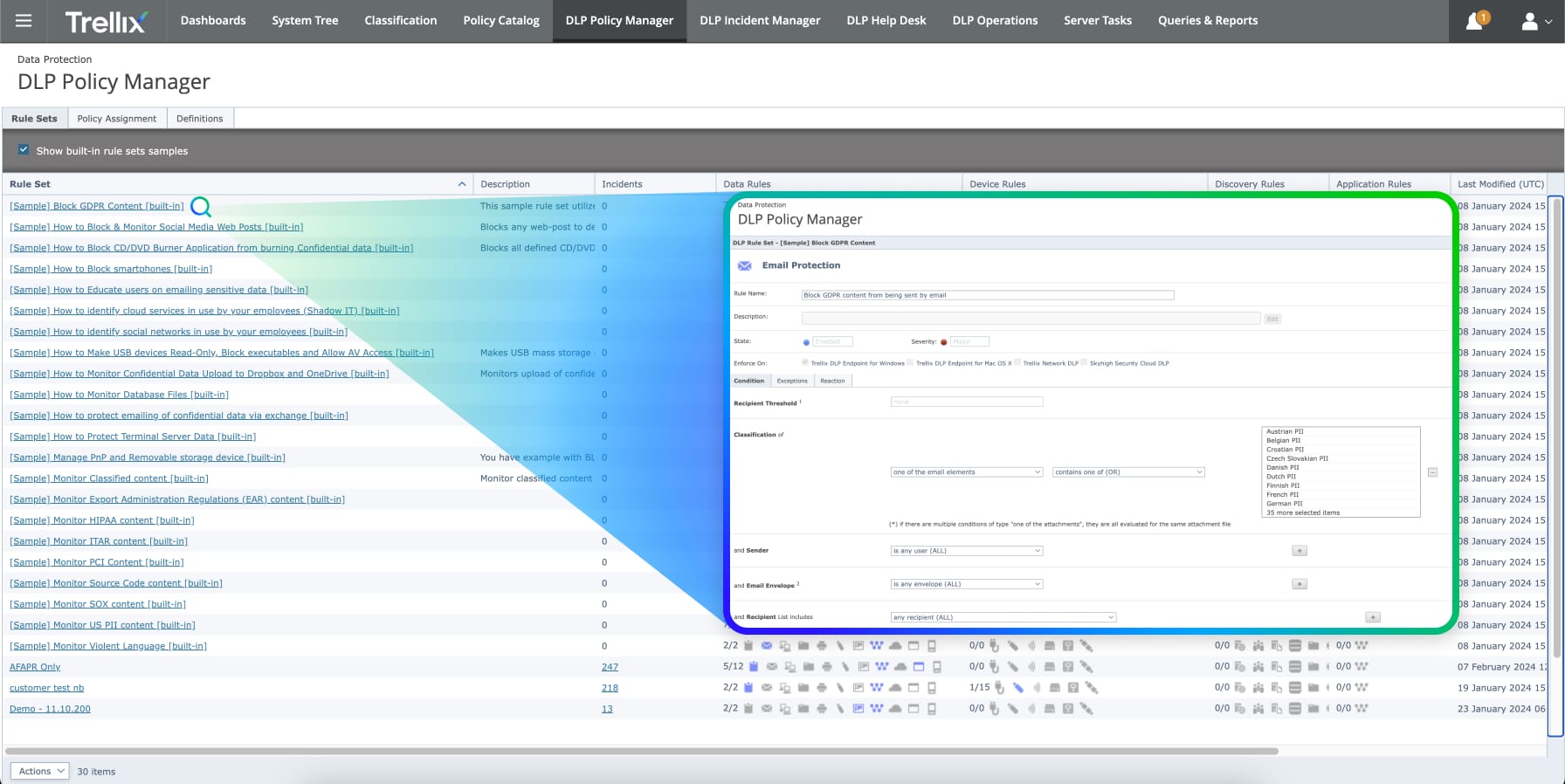
Centralized Monitoring and Event Tracking
Trellix DLP offers a convenient single console to manage deployment, administer policies, monitor events in real-time, and get out-of-the-box reports to ensure compliance.
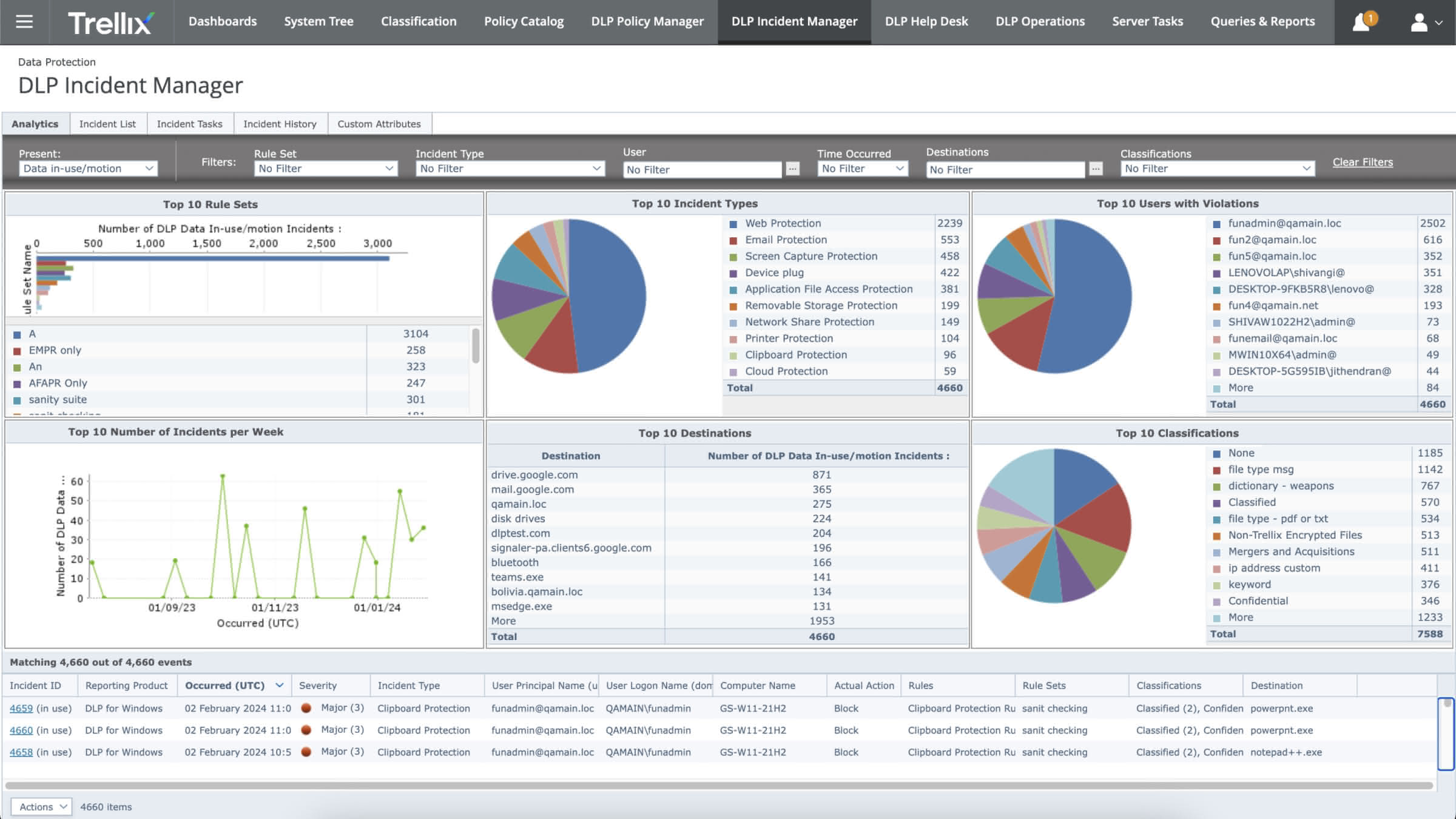
Instant End User Coaching and Notifications
Stop data exfiltration without impacting operations when you customize notifications for users who attempt to violate data-sharing policies and request justification.
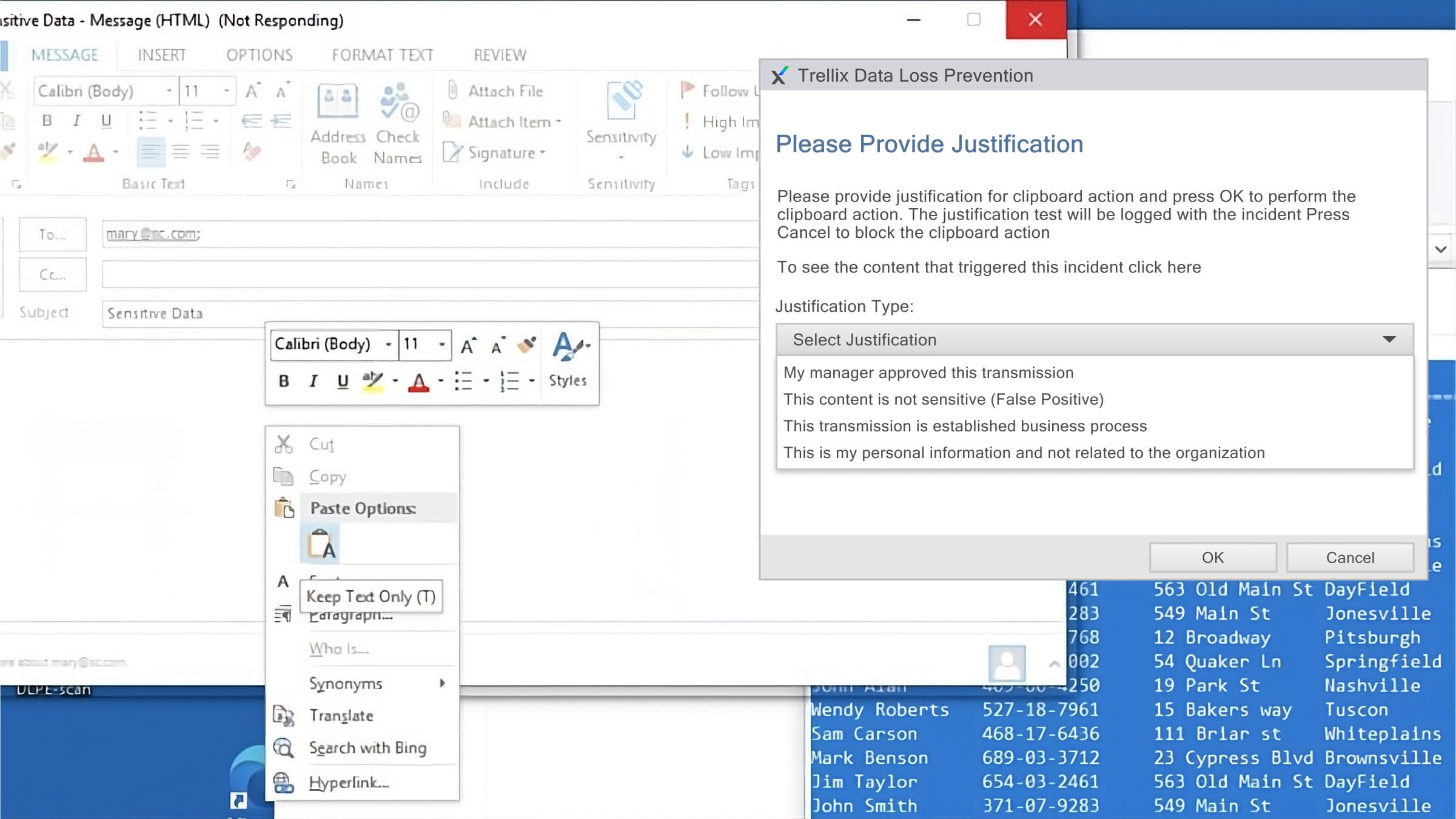
Deploy Policies Across Top Threat Vectors
Choose from out-of-the-box rules or configure your own parameters to find and protect the data that matters to your organization from the keyboard to the cloud.
Trellix Data Loss Prevention Products
Trellix Data Loss Prevention Endpoint Complete
Includes Trellix Device Control, available on-premisis and via SaaS
- Find and classify data on Windows and macOS workstations and servers
- Coach end-users and request justifications for policy exceptions
- Get out-of-the-box compliance features, including reporting
Trellix Device Control
Protect Windows and macOS workstations and servers on-premises or via SaaS
- Prevent unauthorized device installation
- Deploy policies for content-based monitoring, filtering, and blocking
- Available as a stand-alone or included in Trellix DLP Endpoint Complete
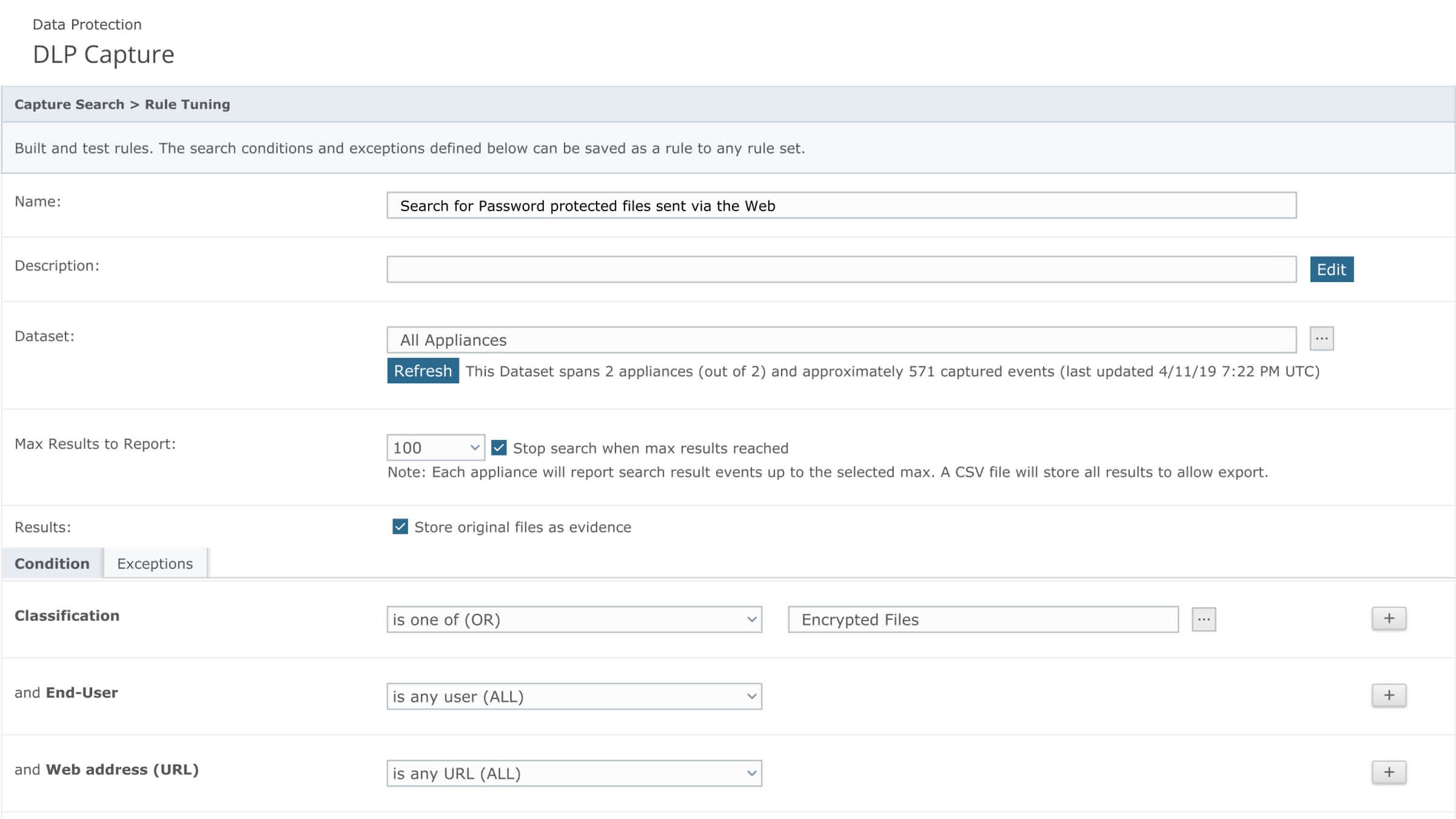
Trellix Data Loss Prevention Discover
Inventory senstive data across networks, storage and database locations.
- Find and classify sensitive data across more than 400 file types
- Capture and retain data to aid forensics and investigations, add on for OCR
- Support compliance activities and reporting out of the box
Trellix Data Loss Prevention Network Monitor
Visibility for sensitive data shared across networks.
- Scan, analyze, and detect network data events in real time
- Collect information to speed invesidations , add on for OCR
- Support compliance activities and reporting out of the box
Trellix Data Loss Prevention Network Prevent
Prevent users from sharing unauthorized information across networks.
- Integrates policies with email and web gateways to protect sensitive information
- Captures information to support investigations, forensics, add-on for OCR
- Support compliance activities and reporting out of the box
