Trellix Intelligent Virtual Execution
Scan objects for threats at any point in your workflow
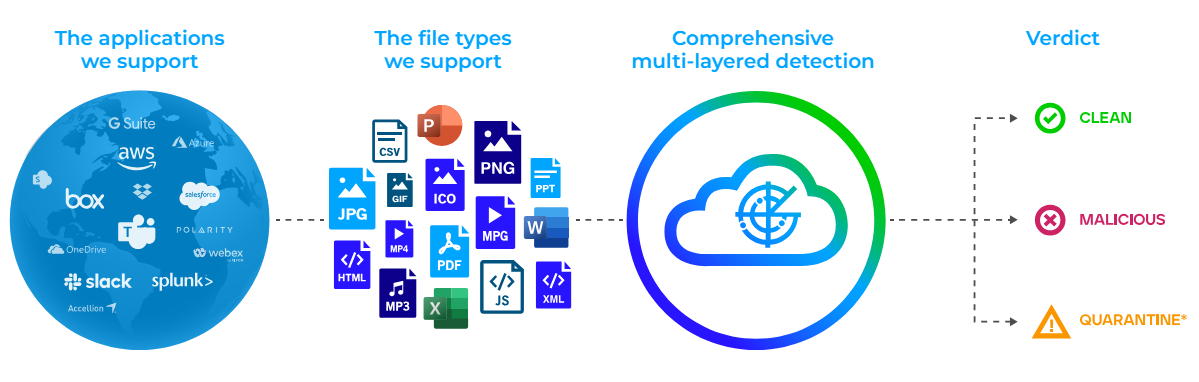
How Intelligent Virtual Execution works
To accurately detect and stop dynamic, never-before-seen exploits and malware, organizations need intelligence-led threat detection that evolves at the speed of the threat space. They also need contextual insight to accelerate resolution of security incidents with concrete evidence, actionable intelligence, and frictionless workflow integration.
IVX is a signature-less, dynamic analysis engine that captures and confirms zero-day, and targeted APT attacks. IVX identifies attacks that evade traditional signature-based defenses by detonating suspicious files, web objects, URLs, and email attachments within a proprietary hypervisor instrumented for over 200 potential simultaneous executions. IVX accelerates incident response by enabling analysts to visualize how malware is behaving within the virtual image and securely interact with malware to test effectiveness of countermeasures.
Available on prem or as a cloud-native service Trellix IVX delivers proven, flexible analysis capabilities wherever you need to quickly inspect and verdict potentially malicious content. SOC analysts can manually submit objects for inspection and insight. Or seamlessly integrate IVX with enterprise applications— built or bought—for continuous and frictionless protection.
Trellix Intelligent Virtual Execution stops incursion by revealing never- before-seen exploits and malware. Using the same proven detection methodologies that power many of our Trellix products, the IVX engine captures and confirms zero-day, multi-flow and other evasive attacks by detonating suspicious files, web objects, URLs, and email attachments.
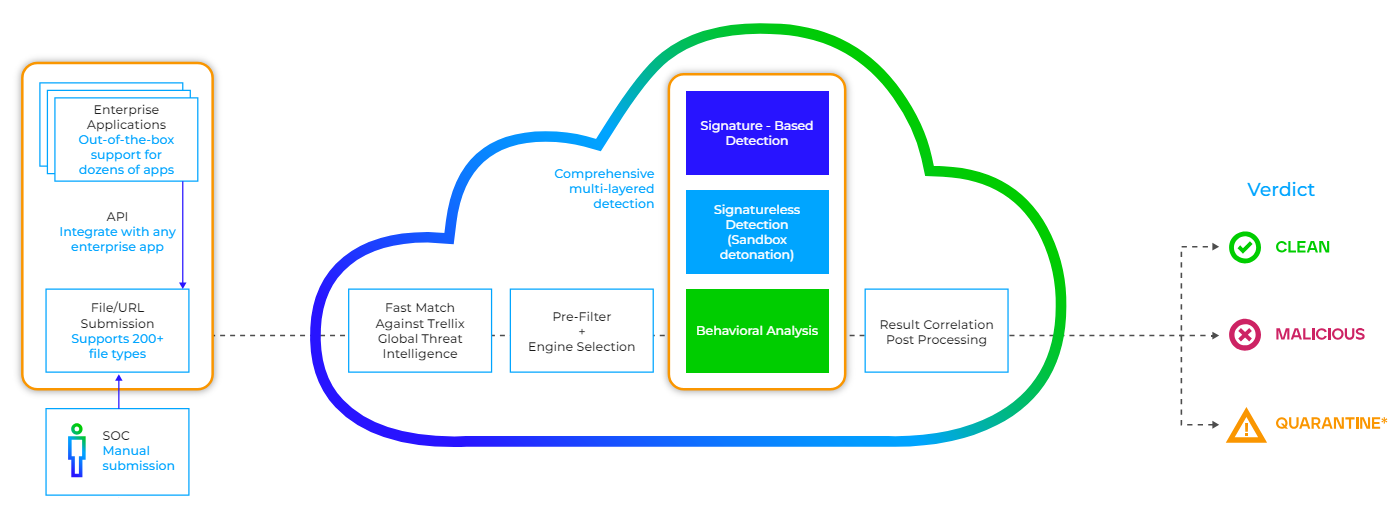
Intelligent Virtual Execution begins by comparing your submission to threat actors’ latest known tactics and other potentially malicious behaviors using Trellix Global Threat Intelligence gleaned from over 40,000 Trellix customers and partners worldwide.
IVX then uses statistical analysis, artificial intelligence, and machine learning to conduct one-to-many analysis. At the time of analysis IVX decides how an object is to be analyzed and composes multiple unique execution environments in real time. IVX conducts over 200 simultaneous executions, covering multiple operating systems, service packs, applications, and application versions.
Unlike detection solutions that focus on a single attack object, Trellix IVX performs multi-flow analysis to break down and fully understand the full context of a multistage attack. Stateful attack analysis is critical to trigger analysis of the entire attack lifecycle, from initial exploit to data exfiltration. Trellix also determines the possibility of secondary or combinatory effects across multiple phases of the attack lifecycle to discover never-before- seen exploits and malware.
If the object is malicious, an alert is sent so you’ll know that object needs attention.

Highlights
- Detects known and unknown malware
- Integrates with all major cloud storage solutions and many web applications
- Analyzes threats in multiple operating systems, including Windows, Mac, and Linux
- Compiles in-depth analysis details, including MITRE ATT&CK mapping, extracted objects, IOCs, and more
- Supports plug-ins for browsers and cloud storage
- Delivers contextual analysis of detected malware in JSON format
Key Technology Features
- Actively analyzes unknown code and suspicious web objects – Objects are executed against a range of browsers, plug-ins, applications, and operating environments. The signatureless IVX engine identifies the use of zero-day exploits, confirms a Web attack is underway, and blocks callbacks and subsequent malware downloads over multiple protocols.
- Detonates all email attachments within virtual environments – All attachments can be safely and accurately analyzed to identify zero-day exploits. Beyond signature- and reputation- based systems, the IVX engine can detect if previously legitimate files have been weaponized and sent via spear phishing email to penetrate enterprise defenses.
- Analyzes for weaponized files on network file shares – The IVX engine can be used to scan CIFS-compatible file shares to detect and stop advanced targeted attacks embedded within weaponized Microsoft Office files, images, PDFs, Flash, or ZIP/RAR/TNEF archives.
- Inspect URLs embedded in emails, MS 365 documents, PDF, and archive files, files downloaded through URLs (including FTP links), obfuscated, spoofed, shortened and dynamically redirected URLs, and credential-phishing and typosquatting URLs
- Proprietary virtualization technology – The IVX engine analyzes and confirms true, zero-day malware, such as Trojans, targeted attacks, bots, VM-aware malware, and advanced persistent threats.
- Multi-stage inspection and blocking engine – Verdict known and zero-day attacks while simultaneously eliminating false positives. The multi-stage inspection process unifies virtualization and network security to accurately block advanced malware that are used to penetrate networks and steal resources and sensitive data.
- Custom-built hypervisor with built-in countermeasures designed specifically for malware analysis. This hypervisor enables peak performance and the ability to detect sandbox aware and evasion tactics used by many sophisticated malware objects.
Accelerate investigation and response
Available on prem or as a cloud-native service, Intelligent Virtual Execution rapidly scans submitted content to identify malware.
You can easily configure access to Intelligent Virtual Execution through an API for easy integration into your security operations center workflow.
In addition to receiving a verdict, you also get supporting contextual detail, such as file, registry, process, and network changes, as well as MITRE ATT&CK mapping and other relevant findings from continually updated Trellix Global Threat Intelligence.
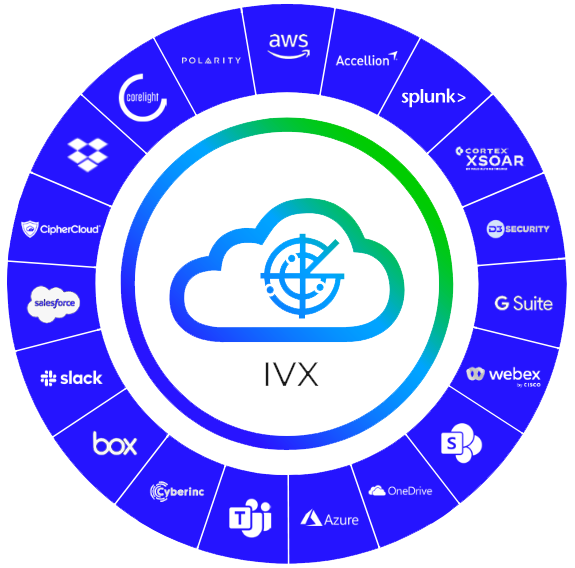
Protect collaboration platforms and enterprise applications
Intelligent Virtual Execution integrates with cloud services like AWS and Azure, collaboration platforms such as Slack, MS 365 and Google Workspace and cloud storage tools like Dropbox, Box, OneDrive.
It also integrates with many enterprise applications such as Salesforce, Webex, Slack, Microsoft Teams, and much more. You can easily integrate with applications that don’t already have a plug-in through our easy-to-use API.